Diplomat MFT Enterprise SFTP SERVER Solution
SFTP is the best choice for file exchanges because it supports the highest levels of security for one- or two-factor authentication, data encryption, and integrity verification.
Need an enterprise level SFTP Server Solution? Try Diplomat MFT
Coviant Software offers an SFTP server option as a part of the Diplomat MFT family of products. Our SFTP server provides out-of-the-box, no-code simple file transfer process automation, PGP encryption, compression operations, and enterprise-grade scalability to support organizations of any size with secure file transfers of any volume. And Diplomat MFT comes with intuitive, web-based administration with an easy to navigate user interface that is deployed behind your firewall to maximize security.

What is an SFTP Server and Why do You Need One?
An SFTP Server is software that you deploy in an internet-facing location so that you can host or receive files for secure file exchanges with your clients, customers, suppliers, and other business partners. External entities connect to your server using any standard SFTP client, using strong authentication and the highest levels of security. SFTP is the best choice for file exchanges because it supports the highest levels of security for one- or two-factor authentication, data encryption, and integrity verification. SFTP is also a universal protocol, available on any platform from Windows, Linux, MacOS, mainframes, IoT, and cloud storage providers. Furthermore, SFTP is a firewall-friendly protocol, requiring only one hole in the firewall to support all file transfer operations (no more headaches with FTP port ranges!).
An SFTP server provides assurances that an organization’s file exchanges with external parties will be handled securely across any network by using the strongest cryptography available to prevent–interception or manipulation by malicious actors via man-in-the-middle attacks.
When combined with our Coviant Software Edge Gateway, the SFTP Server brokers SFTP traffic from your DMZ to the back-end network without requiring any inbound holes in your back-end firewall. This ensures that no data remains in the DMZ, and all authentication and access control is securely managed by your back-end systems. This defense-in-depth approach significantly increases your company’s security posture.
Furthermore, when combined with the award-winning, no-code simple Diplomat MFT automation platform, the files exchanged with our Diplomat SFTP Server can be automatically PGP encrypted or decrypted, ZIP compressed or decompressed, and/or transferred to internal or cloud storage systems where they need to go for integration or consumption. The entire process for file exchanges—send, receive, host, and retrieve—are handled by Diplomat MFT with visibility, management, auditing, and alerting built in.
An SFTP server supports information security and data privacy compliance programs such as HIPAA / HITECH, SOX, GLBA, GDPR, DPA, and PCI-DSS, as well as business-to-business file transfers requiring compliance with organizational standards.
Video walk-through with our CEO; Greg Hoffer
installation and configuration of the Coviant Software Edge Gateway, and the Diplomat MFT SFTP Server
Step-by-Step Installation Process
Configuration and Additional Features
Edge Gateway Magic - SFTP without Firewall Holes
EXPAND FOR VIDEO TRANSCRIPT
Hi. In this video, I will walk you through the installation and configuration of the Coviant Software Edge Gateway, and the diplomat MFT server. For the purposes of this demo, I will be using this single virtual machine that I host in Azure. In a real-world environment, you would put your edge gateway into a DMZ where your servers and external mail servers are, for example, and the Diplomat MFT would be on a secure backend network.
The magic of the edge gateway is that external parties can connect over SFTP to your diplomat MFT server in the back end without requiring any inbound holes in the firewall. So in my example here, we can see that I am allowing Port 2112 in from external, uh, from the public facing internet into my Azure virtual machine.
This will be where I host the SFTP services in the DMZ. Right, so here I have my machine up and running. Let me show you a quick diagram of what we’re going to be doing today. Although this is on one physical machine. For purposes of this demo, this is effectively the solution architecture that we’re talking about inside the internet facing DMZ.
I will be installing the edge gateway. Alongside other internet facing services like mail servers, web servers, et cetera. In this case, I’m exposing port 2112 to the internet where my customers, clients, suppliers, and partners can use their SFTP client represented by the laptop on the left, connect over port 2112 to SFTP.
And what happens is it is magically brokered to the backend sftp server back here, Coviant Software Diplomat. MFT and the SFTP server are in your trusted network. I have my SFTP server on the back end listening to port 22, the standard SFTP port, just to show you that it’s not connecting directly to it. And what’s going to happen is when these two are configured, the SFTP Server will reach an outbound connection to the Edge gateway over port 26841.
By default, it’s configurable, and that establishes what we refer to as the peer notification channel over which messages are passed back and forth. For example, when a client comes in requesting an SFTP connection, it will send a message back over that bidirectional channel. Even though it requires no inbound holes in the firewall, it will say, here comes a connected client.
At that point, SFTP server reaches out over the data port 7638 to establish another socket. And then the Edge Gateway simply brokers the traffic from the client to the server. Never decrypting it, never inspecting it, never changing it. So no secure data ever is visible or stored inside the DMZ. All right, so that’s the architecture.
Let’s see how it works.
Step one is you download and install the Diplomat server. Diplomat MFT server, and the Edge Gateway, which I have done here, and they’re already installed. You can see when I install them. I’ve got two new services, my service control manager, Edge Gateway, and in this case Diplomat trial. Or if you bought a license, it would be Diplomat MFT 64.
It’s very important that before you start the service, go ahead and assign it a log on account. In this case, I use a local system that I comically refer to as Booker, but go to your log on tab and pick a local account. That way you can control the access to the data that these services get to, through that account.
For example, the program files folder or the program data folder. All right, so I’ve got both of these installed changes, user account. Now I can start them. So I’ll start one and the other, and then we’ll see how they are configured. So they’re starting up, they’re both running. Let’s start with the Edge Gateway.
If I install the Edge Gateway on a machine inside my DMZ, I’ve got to configure it so that, uh, I choose the ports over which it listens for external connections and these ports right here, it’s fundamentally all you have to do. So let’s go to the Edge Gateway. Uh, by the way, when you install it, you do get shortcuts installed on your desktop or you can just bookmark it.
It’s a web-based administration utility. By default the admin UI for the Edge gateway is on Port 9273. Note that this is plain text, not HTTPS, and that is because we only listen to local hosts. You can only access the server, through local host or 127 not internet accessible. It’s a very lightweight, set and forget kind of configurations.
So rather than mucking with SSL certificate and stuff, you just connect to it locally. No traffic ever leaves the box. And here we’ll log in. Default password is going to be diplomat, all lowercase. And when you log in the first time, you can change that password here. All right, so the configuration screen on the left-hand side, much like our diagram is, what are you listening to SFTP connections for?
So in this case, I choose the IP address that I want to listen. If I listen to Lo, local Host, external connections won’t be able to reach me. So it’s usually an IP address or all incoming. In a secure environment, you’re going to separate, across two network cards, right? So you’re going to have a network card on this side with its own IP address that listens to inbound connections and a network card on this side that listens for connections from the secure backend network to isolate those two and protect them from firewall access, right? So I’m listening on this IP address. I’m listening to port 2112 for SFTP, and over on the right hand side, different network card in this case. To simplify it, I’m just listening to all incoming. And these are my ports, like illustrated in the diagram.
That’s the configuration to make it work. There are a few other things you can do, if you configure. Which is one server. This part doesn’t really matter, but it, let’s say you have a failover mechanism, or you purchase two edge gateways combined with two Diplomat MFTs on the back end. Then you can use round robin.
So imagine this diagram with another SFTP server for resiliency and another Edge Gateway. Both SFTP servers can connect to this edge gateway. And edge gateway has the policy of saying, how do you want me to direct traffic? It’s either round robin. Which directs traffic from clients to a specific server and then goes to the next one and just rotates between them.
Except I’m going to use sticky sessions, which means an incoming client based upon their IP address. If they make multiple connections, then they will all go to the same Target SFTP server based upon that IP Connection. That way if there’s a particular user using FileZilla, when SCP or some utility, it opens multiple connections.
It makes them all go to the same destination, makes things easier. Alternatively, you can have a failover strategy. So for example, all traffic goes to this SFTP server, unless such time is it’s down, and if I can’t reach that server, it’s not connected. I will go to whatever backup SFTP server you provide me, can be anywhere, can be in a different Data Center as long it has, as it has a relatable IP address from the back end to this Edge Gateway.
And in so doing, I will continue to direct traffic there and mark this as the new one, as the primary. And it’s up to you to kind of redirect it back at your convenience. So in this case, you would have a different IP address, right? So, I would have another connection coming in, or I know that it’s the machine located at 10.0.1.134.
So this is my primary but fail over. In this case, easiest, just round rob and leave at default. You can also have IP access controls on this backend network to make sure that these open ports on the firewall are only connectable by certain IP addresses. It’s one or the other. It’s allow everything except you blacklist something else
So in this case, I allow everything except the following, or I deny everything except the following. So this becomes the white list of the only one allowed through. Easiest thing is to secure your firewalls on the back end, in the front end, so that you control it at a firewall level. But this provides additional software protection.
Okay and the rest shows you here is active status. You can leave this window open. We can see that I’ve got one Diplomat MFT connected to me, happens to be the one on local host. I see it right here. And it currently has no active connections, no file transfer, but a screen, it’s good to go. All right, so that’s Edge Gateway configuration.
Now let’s look at Diplomat MFT. Again, I launched the shortcut. I log in. Default password is diplomat. Until you change it. And here’s our diplomat MFT server. When you set up an SFTP server, your first step is to create SSH key pair to strongly identify your SFTP server. So right click on key pairs, create key pair, fill out the values.
In this case, I’ve already done that, so I can now go to SFTP, I’m sorry, settings SFTP server. Notice I have it enabled. I tell it to use the key pair I just created. I pick the root folder where all my SFTP server users will be housed by default. I can’t go above that level. Everything is there or lower in the directory tree.
And if you wish, you can use a UNC path. So if you could put servers, zero one data SFTP, for example, just make sure that the user account under which the service is running has access to this UNC path. Let me undo that. So everyone’s located here. These are the default permissions for the user. these are the pass authentication policies, et cetera.
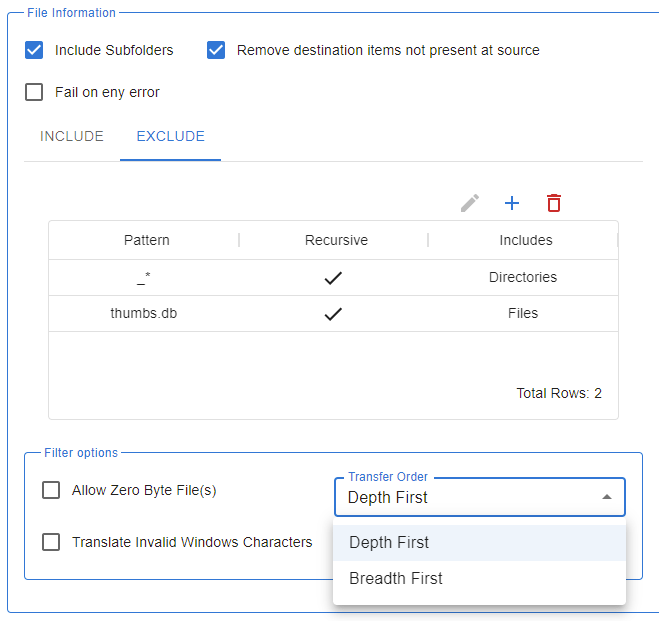
You can even go to advanced settings to pick ciphers, hashes, compression, key exchange algorithms, etc. and we have a feature that allows you to delete files out of user folders that are older than X amount of days. So you don’t explode your disc space. All right, so the basic setting for SFTP server is here, and then the extended setting for Edge Gateway is right here. It’s really simple. I’m going to use the Edge Gateway. Where is the address? Now? Remember, in a real-world scenario, it would be a different machine. It’d be the IP address of this machine and your DMZ. I happen to be running both on the same machine for convenience. So it is located right here on my local machine port number.
And then what’s the identifier for this machine? This is how we can make sure that this Diplomat MFT server announces itself as this unique identifier to the edge gateway, so it can keep track of things. Once it’s on and we click save, then it makes the connection and that’s why we see this as a green connection here.
Oops, it just restarted, so it’ll take a second. All right. So what we see is that Diplomat MFT, on the back end with its SFTP Server is configured, connect this edge gateway. This edge gateway is listening on port 2112 for SFTP traffic. So now let’s finish this by logging in as an external account through port 2112 as SFTP.
And by doing so, we’ll see that it gets brokered all the way through to the backend and it can’t be directly to this back end because that’s listening on port 22. So it must be flowing through the Edge Gateway. So here we have it’s green again because the server SFTP server got its settings changed and restarted and it’s reconnected.
I’m going to drop back down here to my desktop, so I’m no longer in the virtual machine. I’m going to open FileZilla, and I have this configured already under my Azure Edge Gateway test.
You can see it’s connecting to that IP address, I’m sorry, this domain name at Port 2112, and here’s the folders that we see, so let’s double check that. It’s what it should be. Remember that under my SFTP Server, I have this as the root, so we’ll see what the contents of this. And under my SFTP users, I have configured this. So I have one user named Foo. Home folder is foo. So that’s a sub folder of the route and they can’t go any higher than that. So if I look inside the Foo folder, this is what belongs to foo. And sure enough basic rollout that’s here.
And if I transfer files from my local machine up to that Azure machine through the Edge Gateway, We can see that some of ’em are still in progress, but here they go. They’re all up on the remote site, and if I look inside my actual physical machine, here they are here. All right, so that’s the overview of installation and configuration of the Edge Gateway and the Diplomat MFT SFTP server.
So you can protect your data from clients, customers, partners, and suppliers flowing through your internet accessible dmz. And securely onto the back end without requiring any inbound holes in the firewall. Thank you very much.
SFTP Server Frequently Asked Questions
What is SFTP?
SFTP is an acronym that stands for Secure File Transfer Protocol (or Secure Shell File Transfer Protocol) and was developed as a replacement for the unsecure File Transfer Protocol (FTP). It is a standard protocol for securing data transfers and transmissions.
Why is SFTP so popular?
SFTP was designed to be platform independent and is supported nearly universally on systems running Windows, MacOS, Linux, Unix, and other operating systems. This means that data transmissions between otherwise incompatible end points can be done securely.
Why is SFTP support important?
Technology platforms that support SFTP ensure security for data in transit, while also supporting complementary security processes like authentication. As an industry standard protocol, organizations like JP Morgan and CitiBank require that digital trading partners use managed file transfer solutions that support SFTP, such as Diplomat MFT.
Do all managed file transfer products support SFTP?
No! Not all MFT products support SFTP, requiring the user to use other means of security for data in transit. When choosing a managed file transfer solution that will handle high-value data and information protected under mandates like HIPAA, GLBA, SOX, GDPR, and others is it imperative that the product has native support for SFTP.
What is an Enterprise SFTP Solution?
An enterprise SFTP solution is a secure file transfer protocol (SFTP) software tailored for business use. These solutions are distinguished from free or open-source SFTP software by offering several key advantages:
- Security: Enterprise SFTP solutions provide robust security features, including encryption, authentication, and authorization, ensuring data protection from unauthorized access.
- Scalability: They can adapt to the requirements of businesses, whether small or large, accommodating various file transfer needs.
- Reliability: Enterprise SFTP solutions deliver consistent performance even during large file transfers or concurrent connections.
- User-Friendly: These solutions are designed for ease of use with intuitive interfaces, making them accessible to a wide range of users.
- Support: Vendors typically offer support, including technical assistance, training, and documentation.
When implementing an enterprise SFTP solution:
- Choose Wisely: Select a solution that aligns with your business’s size, file types, and security/compliance requirements.
- Plan Integration: Strategize how to integrate the solution into your existing IT infrastructure and train your users.
- Thorough Testing: Before deploying, rigorously test the solution with different file types and under varying load conditions.
- Ongoing Monitoring: Continuously monitor the solution to ensure performance and security.
Regarding Managed File Transfer (MFT) and its relevance to enterprise SFTP solutions:
MFT automates and manages file transfers between systems and applications, supporting various protocols, including SFTP. Integrating MFT with enterprise SFTP solutions enhances the file transfer process:
Benefits of MFT Integration:
- Increased Efficiency: MFT automates SFTP transfers, freeing up IT resources for other tasks.
- Error Reduction: Centralized file transfer management through MFT minimizes errors.
- Enhanced Security: MFT provides centralized control over SFTP user accounts and permissions, bolstering security.
- Compliance Support: MFT generates reports on SFTP activity, aiding in regulatory compliance.
In conclusion, combining enterprise SFTP solutions and MFT creates a secure, reliable, and efficient file transfer system suitable for businesses of all sizes.
CASE STUDIES

READ THE FULL CASE STUDY
CUSTOMER:
CHRISTUS HEALTH
COVIANT PRODUCT:
DIPLOMAT MFT ENTERPRISE EDITION

READ THE FULL CASE STUDY
CUSTOMER:
CONRAIL
COVIANT PRODUCT:
DIPLOMAT MFT STANDARD EDITION

READ THE FULL CASE STUDY
CUSTOMER:
MOLINA HEALTHCARE
COVIANT PRODUCT:
DIPLOMAT MFT ENTERPRISE EDITION
HOW DIPLOMAT MFT WORKS
Diplomat’s flexible architecture allows you to select the modules and functionality you need, to meet your organizations secure file transfer requirements, now and as they grow.