Let us know your data transfer requirements and we’ll be in touch
Award-winning Managed File Transfer Software
Diplomat MFT is an award-winning, secure managed file transfer software platform. Do you need to safely and reliably send sensitive files to other organizations? Diplomat MFT is easy to use, works with all the cloud services, and supports the protocols you and your partners use.
Recognized as the best value in secure, managed file transfer, Diplomat MFT delivers enterprise grade performance at a fair price, and we back it up with a passion for customer service. That is why Coviant Software earned the highest rating for software performance and customer service from Software Reviews.
Diplomat MFT is installed on your internal network behind a firewall and transfer files between secure FTP servers, web servers, email servers, file servers and NAS devices, application servers, cloud storage providers, private clouds and other systems both inside and outside your firewall.

ENGINEERED TO PERFORM
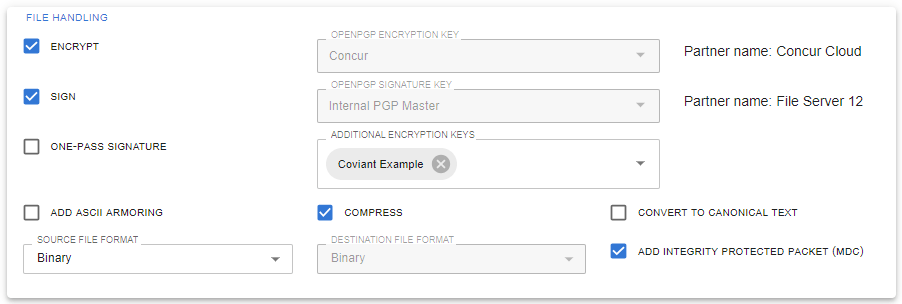
Diplomat MFT is feature rich and designed to address almost any file transfer requirement, with three editions (Basic, Standard, Enterprise) to support every organization and with Edge Gateway and the SFTP Server available to take full control of your most demanding file transfer processes. And you can rely on Diplomat MFT because it is engineered with security standards like SFTP for secure transport, PGP for file encryption, and to easily integrate your managed file workflows with cloud services from AWS, Azure, Google Cloud, Box, Dropbox, Oracle Cloud, Citrix ShareFile, and more.

Terabytes transferred per day
Individual transfers per day
Concurrent jobs
Choosing the Best MFT Software vendor for your business
When it comes to finding the right managed file transfer software solution for your business we understand there are many factors to consider.
Let us guide you through the process.
Diplomat MFT is secure, enterprise-grade managed file transfer software designed as a comprehensive, scalable solution to meet and grow with your file transfer needs. Easy to use and with automations to ensure accurate and efficient workflow creation and execution, Diplomat MFT has what you need at an ethical price.
Installed and running in minutes.
Robust scheduler with limitless capacity
No-code simple operation.
File and transport encryption
Accurately understand your requirements
Coviant Software delivers the industry’s top rated customer service. If you have questions about Diplomat MFT and your organization’s specific needs, we recommend speaking with one of our managed file transfer experts. Our team listens and we will make sure to find the solution that is right for you by guiding you through a:
Live software demonstration
After understanding your requirements, we can walk you and your colleagues through a live demonstration of Diplomat MFT so you can see the software working in real-time and in a context that is meaningful to you.
And if you have new questions or requirements that come to mind, this is the best way to address them.
Transparent, ethical pricing and easy to work with
A trusted partner
After seeing and experiencing Diplomat MFT, should you decide to purchase we make it easy by letting you know what you’re getting and at what price. No hidden fees or costs to get the features you want.
Diplomat MFT comes in three editions that are right-sized for every organization, but at a fraction of what other vendors charge.
Coviant Software prides itself on being an ethical and transparent partner. Diplomat MFT wins awards as the best managed file transfer software, and our customer service is rated best in the MFT industry. If your organization contracts with an integrator or IT reseller, no problem. Just let us know.
We’re happy to work with them to make sure you get what you need.
HOW DIPLOMAT MFT WORKS
Diplomat’s flexible architecture allows you to select the modules and functionality you need, to meet your organizations secure file transfer requirements, now and as they grow.
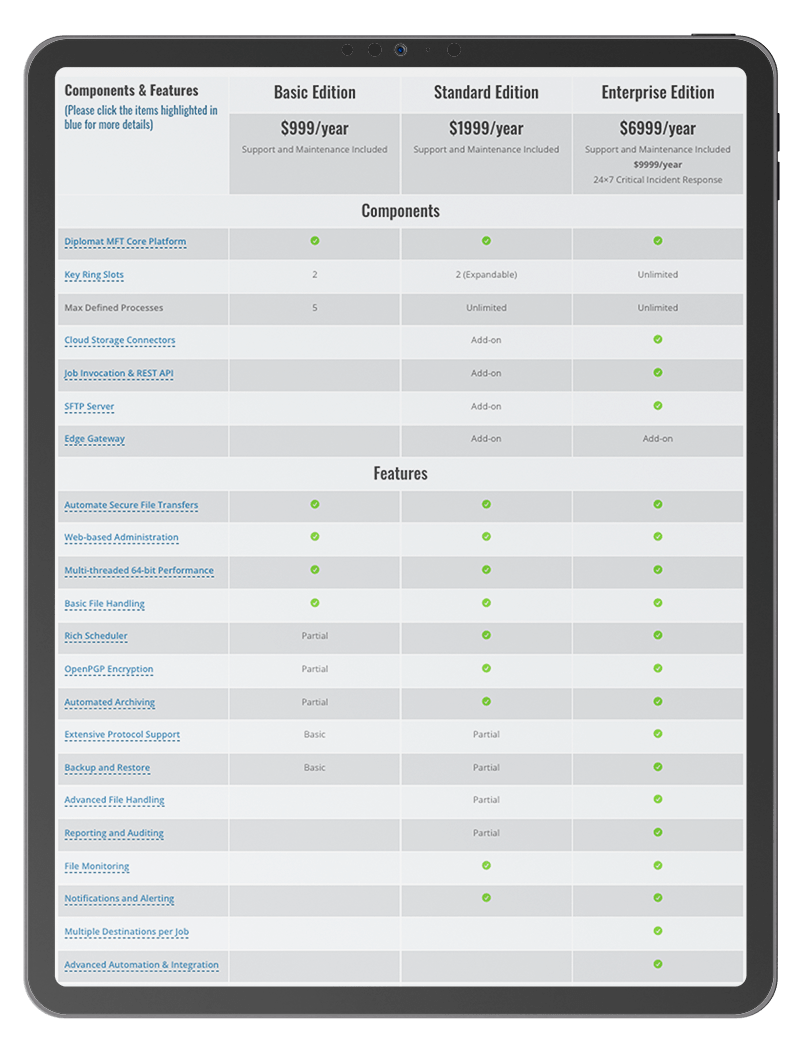
Choose from 3 Editions
We have three editions of Diplomat MFT to suit varying business requirements and budgets.
BASIC EDITION
$999 USD
YEARLY
Diplomat MFT Core Platform
Automate Secure File Transfers
Web-based Administration
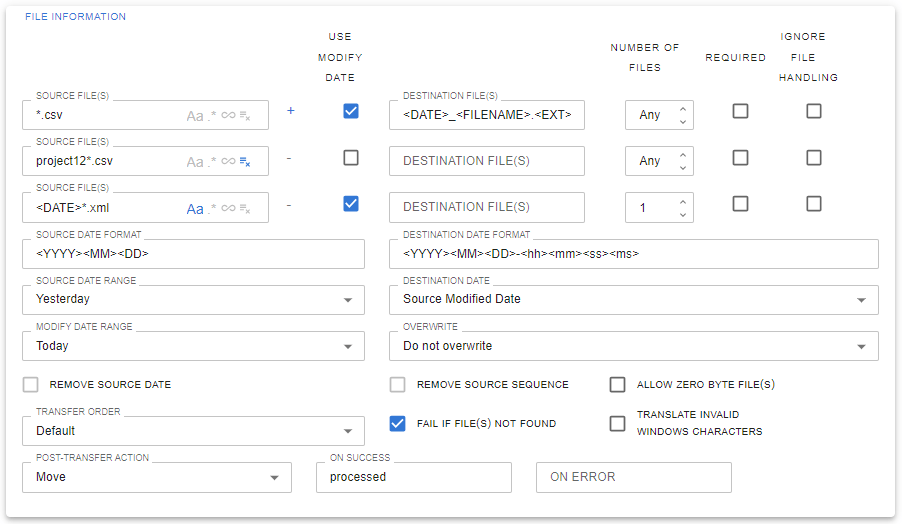
Basic File Handling
Multi-threaded 64-bit Performance
STANDARD EDITION
$2499 USD
YEARLY
OpenPGP Encryption
Rich Scheduler
Automated Archiving
File Monitoring
Notifications and Alerting
Reporting & Auditing
ENTERPRISE EDITION
$9999 USD
YEARLY
Extensive Protocol Support
Advanced File Handling
Distribution, Replication, and Sync
24×7 Critical Incident Response
($14,999/year)
Which Edition Do I Need?
We can help you with your MFT Software Comparison and would be more than help to offer a free demo of Diplomat MFT.

PROFESSIONAL SERVICES FOR DIPLOMAT MFT
Turn-key solutions are critical to achieve success without runaway costs and unexpected delays. Our seasoned experts are available to meet your business goals by delivering professional services. Experienced, attentive, and detail-oriented, you can rely on our team to help yours win big.
MFT EXPERT SERVICES
Health Checks
Our experts will identify what you’re doing right and any opportunities for enhancement.
Implementation Assistance
Hit the ground running in production with help from our seasoned experts.
Upgrades & Training
Our experts will be there with you in real time to guide your upgrades and ensure new capabilities are being used properly.
MFT Solutions
Automating, Securing, and Simplifying Secure File Managed Transfers
Automate PGP & SFTP
With our easy-to-use software, you can automate the PGP encryption and decryption process, ensuring that your files remain secure throughout the transfer process.
HIPAA Compliance
By automating critical elements of the secure file transfer management process, Diplomat MFT can play a vital role in your data privacy and information security program for managing PHI.
How to Automate FileZilla
Filezilla does not provide any way to automate file transfers, but you can import your FileZilla Site Manager data into Diplomat MFT to effortlessly automate your transfers.
Exchanging files with Workday with SFTP
Diplomat MFT can help you to automate your regular file transfers with workday, such as payroll and timesheet data. By automating your Workday transfers, you will save time on repeated manual processes and avoid the risk of human errors.
What is Managed File Transfer?
Managed File Transfer (MFT) software is a technology solution that facilitates the secure, automated, and efficient exchange of files between different systems, both within and outside an organization. It ensures that files, such as documents, data, and media, are transferred reliably, while also providing features like encryption, access control, and auditing to enhance security and compliance. MFT software simplifies and streamlines file transfer processes, reducing manual intervention and the risk of data breaches, making it essential for businesses that require secure and seamless file exchanges.
We have put together a Guide to MFT to help those new to the world of MFT understand What is Managed File Transfer and includes an MFT Webinar with our CEO, Greg Hoffer.
Why is Managed File Transfer important?
Managed File Transfer (MFT) is critically important for organizations across various industries for several key reasons:
Enhanced Data Security:
MFT software prioritizes data security by offering robust encryption mechanisms, both in-transit and at-rest. This ensures that sensitive information remains confidential during the transfer process and while stored on servers. In an era of increasing cyber threats and data breaches, MFT helps protect valuable business data.
Maintaining Regulatory Compliance:
Many industries and regions have stringent data security and privacy regulations. MFT solutions aid in compliance with these regulations by providing features like audit trails, access controls, and secure protocols. This is particularly crucial in sectors such as healthcare (HIPAA), finance (PCI DSS), and the European Union (GDPR).
Streamlined Operations:
MFT automates and simplifies file transfer processes, reducing the need for manual intervention. This streamlines operations, minimizes the risk of human errors, and ensures the timely delivery of files. It also frees up employees’ time to focus on more value-added tasks.
Data Integrity:
MFT solutions often include features to verify the integrity of transferred files. This ensures that files are not corrupted or altered during the transfer process, guaranteeing data reliability.
Auditability and Compliance Reporting:
MFT software maintains detailed logs and audit trails of file transfer activities. This auditability is crucial for compliance reporting and for tracking who accessed, transferred, or modified files, providing transparency and accountability.
Efficient File Transfers:
MFT optimizes file transfer speeds by using advanced algorithms and bandwidth management. This ensures that files are transferred quickly and efficiently, even when dealing with large volumes of data.
Global Accessibility:
With MFT, organizations can securely transfer files across geographical boundaries. This is vital for global enterprises, ensuring that data can be shared seamlessly between international offices, partners, and customers.
Scalability:
MFT solutions are designed to scale with an organization’s needs. As businesses grow and their file transfer requirements increase, MFT can adapt to handle larger volumes of data and more complex workflows.
Reduced Downtime:
MFT solutions often incorporate features like failover and high availability to minimize downtime. This ensures that critical file transfers continue without interruption, even in the event of server failures.
Cost Savings:
While there is an initial investment in MFT software, the automation, efficiency, and security benefits can lead to cost savings in the long run. Fewer errors, reduced manual effort, and improved data security contribute to a strong return on investment (ROI).
In summary, Managed File Transfer (MFT) is significant for organizations as it combines data security, compliance adherence, and streamlined operations. It offers the assurance that files are transferred securely and efficiently, making it an essential tool for businesses that rely on the seamless exchange of data while meeting stringent security and regulatory requirements.
What are the key features of MFT Software?
Managed File Transfer (MFT) software offers a range of essential features designed to secure, automate, and streamline the exchange of files and data within and between organizations. Here are key features of MFT software, along with descriptions of each:
Encryption:
MFT software employs encryption techniques (i.e PGP Encryption) to protect files both in transit and at rest. This ensures that data remains confidential and secure during transfer and storage.
Automation:
Automation is a core feature of MFT solutions. It enables the creation of workflows and tasks that can be scheduled or triggered by specific events. Automation reduces manual intervention, increases efficiency, and ensures consistent file transfers.
Secure Protocols:
MFT supports secure file transfer protocols such as SFTP (SSH File Transfer Protocol), FTPS (FTP Secure), and HTTPS. These protocols use encryption and authentication mechanisms to safeguard data during transmission.
Access Controls:
Access controls allow administrators to define user permissions and roles. This feature ensures that only authorized individuals can access and transfer files, enhancing security and compliance.
Audit Trails:
MFT software maintains detailed logs and audit trails of all file transfer activities. These records include information about who accessed, transferred, and modified files. Audit trails are crucial for compliance reporting and security monitoring.
Integration Capabilities:
MFT solutions integrate with various systems, applications, and cloud services. This integration ensures seamless connectivity and allows for the automation of end-to-end business processes.
File Compression:
MFT software often includes file compression features to reduce the size of files before transfer. This saves bandwidth and speeds up transfers, especially for large files.
File Conversion:
Some MFT solutions offer file format conversion capabilities. This can be useful when files need to be converted from one format to another during the transfer process.
High Availability:
High availability features ensure uninterrupted file transfers, even in the event of server failures or network disruptions. Redundancy and failover mechanisms are typically included.
Workflow Automation:
MFT software enables the creation of complex workflow automation. Workflows can include conditional logic, routing rules, and decision points to orchestrate file transfers and associated processes.
File Tracking and Notifications:
Users can track the status of file transfers in real-time. Notifications and alerts can be configured to inform stakeholders about successful or failed transfers.
File Expiry and Purging:
MFT software allows organizations to set file expiration dates and automated purging rules. This ensures that files are retained only as long as necessary for compliance and operational needs.
Load Balancing:
Load balancing capabilities distribute file transfer workloads evenly across multiple servers or nodes, improving performance and reliability.
Reporting and Analytics:
Comprehensive reporting and analytics tools provide insights into file transfer activities, usage trends, and compliance status. This helps organizations make informed decisions.
Multi-Platform Support:
MFT solutions are compatible with various operating systems, including Windows, Linux, and Unix, ensuring flexibility and interoperability.
These key features collectively enable organizations to manage file transfers securely, efficiently, and in compliance with regulatory requirements. The specific feature set may vary among different MFT software providers, so organizations should evaluate their needs and select a solution that best aligns with their requirements.
How Does MFT Differ from FTP?
Managed File Transfer (MFT) and traditional FTP (File Transfer Protocol) serve the purpose of transferring files, but they differ significantly in terms of features, security, and functionality. Here, we highlight the key differences between MFT and FTP, including an example of the popular FTP client, FileZilla:
- Security:
FTP: FTP transfers data in plaintext, making it susceptible to eavesdropping and data interception. It lacks built-in encryption.
MFT: MFT emphasizes security and provides robust encryption mechanisms, including both in-transit (e.g., SFTP, FTPS) and at-rest encryption. This ensures data confidentiality and integrity during transfers.
- Automation:
FTP: FTP clients like FileZilla require manual intervention for each file transfer. Automation capabilities are limited.
MFT: MFT solutions offer powerful automation features, allowing users to create complex workflows and schedules. Tasks can be automated based on triggers, reducing manual effort.
- Compliance:
FTP: FTP does not inherently support compliance with data security regulations. Meeting regulatory requirements requires additional effort.
MFT: MFT solutions are designed with compliance in mind and include features such as audit trails, access controls, and secure protocols to help organizations meet regulatory standards (e.g., HIPAA, GDPR).
- User Management:
FTP: User management in FTP is basic, and permissions are often limited to directories. Authentication may rely on basic username and password.
MFT: MFT solutions offer advanced user management with granular permissions, role-based access controls, and support for various authentication methods, including multi-factor authentication (MFA).
- Centralized Control:
FTP: FTP servers and clients are typically standalone, making centralized control and monitoring challenging.
MFT: MFT solutions provide centralized control, allowing administrators to manage and monitor all file transfers from a single interface.
- Scalability:
FTP: Scaling FTP setups can be complex, requiring additional servers and manual configuration.
MFT: MFT solutions are designed for scalability, enabling organizations to handle increasing file transfer demands efficiently.
- Reliability:
FTP: FTP lacks built-in mechanisms for ensuring reliable file transfers. Errors can occur without automatic recovery.
MFT: MFT solutions include features like retry mechanisms and error handling, ensuring the reliability of file transfers.
- Reporting and Monitoring:
FTP: Basic reporting is available, but it often requires manual extraction of log files.
MFT: MFT solutions offer comprehensive reporting and monitoring tools, enabling real-time visibility into file transfer activities.
FileZilla (FTP Client) vs MFT Software:
FileZilla is a popular FTP client that supports FTP and FTPS. It is known for its simplicity and ease of use.
If an organization using FileZilla were to switch to MFT, they would gain enhanced security through protocols like SFTP or FTPS, automation capabilities for scheduled transfers, improved compliance support, centralized control and monitoring, and advanced user management features.
In summary, MFT offers advanced features, security, automation, and compliance support that traditional FTP lacks. While FTP may still be suitable for simple file transfers, organizations with stringent security and compliance requirements often prefer MFT solutions to ensure the confidentiality and integrity of their data during transfers.
How Can I Implement MFT in My Organization?
Implementing Managed File Transfer (MFT) in your organization involves several key steps to ensure a smooth and secure transition. Here are insights into the implementation process, including best practices and potential challenges:
- Needs Assessment and Planning:
- Identify Requirements: Begin by defining your organization’s specific file transfer needs, including the volume of data, security requirements, compliance obligations, and integration needs.
- Choose the Right MFT Solution: Research and select an MFT solution that aligns with your requirements. Consider factors such as scalability, security features, automation capabilities, and compatibility with your existing systems.
- Infrastructure Setup:
- Server Deployment: Set up MFT servers, whether on-premises or in the cloud, based on your chosen solution. Ensure that the servers meet system requirements.
- Network Configuration: Optimize your network infrastructure to support secure and efficient file transfers. Configure firewalls, ports, and network security policies as needed.
- Security Considerations:
- Access Controls: Implement granular access controls to restrict user permissions and ensure that only authorized individuals can access and transfer files.
- Encryption: Configure encryption mechanisms (e.g., SFTP, FTPS) to safeguard data during transit and at rest. Ensure proper key management.
- Authentication: Implement strong authentication methods, including multi-factor authentication (MFA), to enhance security.
- Integration and Automation:
- Integrate with Existing Systems: Ensure that your MFT solution integrates seamlessly with your existing applications, databases, and systems. This may require developing custom connectors or APIs.
- Automation Workflows: Design and implement automated file transfer workflows that align with your business processes. Consider factors such as scheduling, event triggers, and conditional logic.
- Testing and Quality Assurance:
- Testing: Thoroughly test the MFT implementation, including file transfers, automation workflows, and security features. Conduct testing in a controlled environment to identify and address issues before deployment.
- Quality Assurance: Implement quality assurance processes to validate that file transfers meet performance expectations and compliance requirements.
- User Training and Documentation:
- Training: Train users and administrators on how to use the MFT solution effectively. Provide guidance on best practices, security protocols, and troubleshooting.
- Documentation: Create comprehensive documentation that includes user guides, troubleshooting procedures, and system configurations for reference.
- Deployment and Monitoring:
- Deployment: Gradually roll out the MFT solution to different teams or departments, monitoring its performance and addressing any issues that arise.
- Monitoring: Implement robust monitoring and alerting mechanisms to track file transfer activities, errors, and security incidents in real-time.
- Compliance and Reporting:
- Compliance: Ensure that your MFT implementation complies with industry-specific regulations (e.g., HIPAA, GDPR) and internal data security policies.
- Reporting: Leverage reporting and analytics tools provided by the MFT solution to generate compliance reports and gain insights into file transfer activities.
- Ongoing Maintenance and Optimization:
- Regular Updates: Keep the MFT software and systems up-to-date with the latest patches and security updates.
- Optimization: Continuously monitor and optimize your MFT implementation to improve performance, security, and efficiency.
Potential challenges when introducing MFT into your business for the first time can include the following:
- Complexity: MFT implementations can be complex, especially in large organizations with diverse IT environments.
- Integration Issues: Integrating MFT with existing systems may pose challenges, requiring custom development work.
- Security Risks: Ensuring robust security measures and staying compliant can be challenging.
- User Adoption: Encouraging users to adopt the new solution and adhere to security protocols may require change management efforts.
Successful MFT implementation involves careful planning, thorough testing, ongoing monitoring, and user education. It’s essential to work closely with IT teams, consider potential challenges, and leverage the expertise of MFT vendors or consultants if needed to ensure a successful transition to Managed File Transfer.
What are some actual industry examples of where managed file transfer software is used?
Managed file transfer (MFT) software is used across various industries to address specific data transfer needs and enhance security, efficiency, and compliance. Here are some industry examples where MFT software finds application:
Healthcare: In healthcare, MFT software ensures secure and compliant transfer of patient records, medical images (e.g., X-rays, MRIs), and other sensitive healthcare data between hospitals, clinics, and insurance providers while adhering to regulations like HIPAA.
Financial Services: Financial institutions use MFT software to securely exchange financial data, transaction records, and customer information with other banks, payment processors, and regulatory bodies while complying with financial regulations like PCI DSS.
Manufacturing: Manufacturing companies employ MFT solutions to automate the exchange of production data, supply chain information, and design files with suppliers, distributors, and production facilities, improving operational efficiency.
Retail and eCommerce: Retailers and eCommerce businesses use MFT software to manage the transfer of product catalogs, inventory data, and customer orders between systems, warehouses, and online platforms to ensure real-time updates and order fulfilment.
Government and Public Sector: Government agencies utilize MFT solutions to securely exchange sensitive information such as tax data, legal documents, and citizen records while adhering to strict compliance standards and data protection laws.
Energy and Utilities: Energy companies leverage MFT software to facilitate the transfer of data from remote sensors and monitoring equipment, ensuring the seamless flow of information for grid management and reporting.
Aerospace and Defence: In the aerospace and defence sector, MFT is used for sharing design documents, specifications, and project files securely with contractors, partners, and regulatory agencies, often subject to ITAR compliance.
Legal Services: Law firms use MFT solutions to exchange confidential legal documents, contracts, and evidence securely with clients, opposing counsel, and court systems, maintaining attorney-client privilege.
Education: Educational institutions employ MFT software to securely share student records, research data, and administrative documents among various departments, faculty, and educational partners while ensuring FERPA compliance.
Logistics and Transportation: Logistics companies and transportation providers use MFT to optimize the transfer of shipment data, tracking information, and customs documentation with partners, carriers, and customs authorities.
Media and Entertainment: Media companies use MFT for the secure exchange of large video files, digital media content, and advertising materials among production teams, broadcasters, and distribution platforms.
Pharmaceuticals and Life Sciences: Pharmaceutical companies employ MFT software for the secure transfer of drug development data, clinical trial results, and regulatory submissions, ensuring compliance with FDA regulations.
Telecommunications: Telecommunications providers use MFT to manage the transfer of customer billing data, network configuration files, and provisioning data between systems and network operators.
These are just a few examples of industries where managed file transfer software plays a crucial role in ensuring secure, efficient, and compliant data exchange processes. MFT solutions can be customized to meet the specific needs and regulatory requirements of each industry, making them a versatile tool for modern business operations.
Do you have any final advice for when conducting a managed file transfer software comparison?
Choosing the right managed file transfer (MFT) vendor is crucial for ensuring that your business’s data transfer needs are met efficiently and securely. Here are some helpful considerations when conducting a managed file transfer software comparison and review:
1. Security Features:
- Consideration: Evaluate the security features offered by each vendor, such as encryption methods (SSL/TLS, SFTP, PGP), access controls, and data-at-rest protection.
- Importance: Security is paramount when transferring sensitive data, especially in industries like healthcare, finance, and government.
2. Compliance Support:
- Consideration: Check whether the MFT solution supports industry-specific regulations (e.g., HIPAA, PCI DSS, GDPR) and offers compliance reporting features.
- Importance: Compliance is critical in industries with strict regulatory requirements, such as healthcare, finance, and legal services.
3. Integration Capabilities:
- Consideration: Assess the ability of the MFT solution to integrate with your existing systems, including ERP, CRM, and cloud storage platforms.
- Importance: Integration streamlines business processes, making it crucial in industries like manufacturing, logistics, and retail.
4. Scalability:
- Consideration: Determine whether the MFT software can scale to accommodate your organization’s growing data transfer needs.
- Importance: Scalability is vital for industries with fluctuating data volumes, such as retail during peak seasons.
5. User-Friendliness:
- Consideration: Evaluate the user interface and ease of use of the MFT solution. Consider the learning curve for your staff.
- Importance: User-friendly software enhances productivity and reduces training time, benefiting all industries.
6. Performance and Speed:
- Consideration: Test the performance and transfer speed of the MFT software under realistic conditions to ensure it meets your requirements.
- Importance: Industries like media and entertainment require fast data transfer for content distribution.
7. Automation and Workflow:
- Consideration: Explore the automation and workflow capabilities of the MFT solution, including scheduling, triggers, and notification systems.
- Importance: Automation is essential for optimizing processes in industries like manufacturing, supply chain, and energy.
8. Reliability and Uptime:
- Consideration: Research the vendor’s historical uptime and reliability. Look for failover and redundancy options.
- Importance: Reliability is crucial in industries like telecommunications, where downtime can disrupt services.
9. Support and Maintenance:
- Consideration: Examine the vendor’s support options, including technical support, updates, and documentation.
- Importance: Timely support is critical in industries like healthcare, where downtime can impact patient care.
10. Cost and Licensing:
– Consideration: Understand the pricing structure, including licensing fees, subscription models, and any hidden costs.
– Importance: Cost considerations are vital in all industries to ensure the solution aligns with your budget.
11. Vendor Reputation:
– Consideration: Research the vendor’s reputation, customer reviews, and case studies to gauge their track record.
– Importance: Vendor reliability is essential in industries like aerospace and defense, where sensitive data is involved.
12. Customization and Flexibility:
– Consideration: Assess the software’s customization options to tailor it to your specific needs.
– Importance: Customization is valuable in industries like legal services, where unique workflows may be required.
13. Data Transfer Protocols:
– Consideration: Ensure that the MFT solution supports a wide range of transfer protocols (e.g., FTP, SFTP, HTTP/S).
– Importance: Protocol flexibility is essential for compatibility with diverse systems and partners in various industries.
14. Data Analytics and Reporting:
– Consideration: Look for advanced reporting and analytics capabilities to gain insights into file transfer activities.
– Importance: Data analytics are valuable in industries like finance for auditing and compliance purposes.
By carefully considering these factors and conducting a thorough comparison and review of managed file transfer vendors, businesses can make an informed decision that aligns with their specific industry requirements and organizational goals.
Comparing vendors against each other can be challenging due to several factors:
- Specific Requirements: The suitability of an MFT solution depends on the specific needs and requirements of an organization. What may be a disadvantage for one company might be an advantage for another, depending on their unique use case.
- Feature Sets: MFT solutions vary in terms of their feature sets, and what may be a strength in one solution might not be as critical for another organization. It’s essential to evaluate features based on your specific priorities.
- Budget Considerations: Different organizations have varying budget constraints, and what might be cost-effective for one business may not align with the budget of another.
- Company Size: The size of an organization can also impact which MFT solution is the best fit. Smaller companies might prioritize ease of use and cost-effectiveness, while larger enterprises may prioritize scalability and advanced features.
- Industry Requirements: Different industries have unique compliance and security requirements. Some MFT solutions are tailored to specific industries and regulatory standards, making them a better fit for organizations in those sectors.
- Vendor Reputation: Vendor reputation can vary, and the perception of a vendor’s reputation may be influenced by factors such as customer support, reliability, and past experiences.
To conduct a fair and accurate comparison, it’s essential to assess MFT solutions based on your organization’s specific needs, industry requirements, budget, and scalability demands. Consider conducting a detailed evaluation, potentially with the assistance of a qualified IT consultant, to ensure you select the MFT solution that aligns best with your unique circumstances.
Is Diplomat MFT capable of Enterprise File Transfer?
At its core, Diplomat MFT is enterprise-grade managed file transfer, designed to handle complex and secure data transfers at scale. Coviant Software customers, including some of the largest healthcare networks in the country, rely on Diplomat MFT to send, receive, host, and retrieve their most sensitive files. Here’s a brief list of the strengths and capabilities Diplomat MFT brings to bear:
Features for Enterprise File Transfer:
- Scalability: Diplomat MFT can handle large volumes of file transfers securely and efficiently, making it suitable for even the most demanding enterprise environments. And our robust scheduler can handle a virtually unlimited number of concurrent jobs.
- Security: It offers robust security features like PGP encryption, digital signatures, and multi-factor access control to ensure the confidentiality and integrity of your data.
- Automation: Automate repetitive file transfer tasks with workflows and schedules to ensure accurate transfers, minimize the risk of human error, freeing your IT and administrative staff for other important work.
- Compliance: Diplomat MFT helps you comply with government regulations and industry standards like HIPAA, PCI DSS, and GDPR by providing detailed audit trails and reporting.
- Integrations: Diplomat MFT works seamlessly with many popular business applications like ERP and CRM platforms, and cloud storage services like Amazon S3, Google Cloud, Azure Blob, Oracle Cloud, Citrix ShareFile, Box, DropBox, and more.
- Ease of Use: Diplomat MFT offers a user-friendly interface that makes it simple for even non-technical users to manage file transfers.
- Value: With Coviant Software you get a lot, but you don’t have to pay a lot. We believe cost should not be a barrier to secure file transfers, so we price Diplomat MFT fairly and ethically—then back it up with the industry’s best-rated customer and technical support.
Editions for Different Needs:
Diplomat MFT comes in three right-sized editions to cater to the needs of every enterprise:
- Basic Edition: Ideal for small businesses with limited file transfer requirements.
- Standard Edition: Offers additional features like scheduling, triggers, and file compression for medium-sized businesses.
- Enterprise Edition: Provides the most comprehensive feature set, including advanced security, auditing, and workload management for large enterprises.
Overall, Diplomat MFT is a powerful and versatile solution for enterprise file transfer. Its combination of scalability, security, automation, and ease of use makes it a great choice for businesses of all sizes.
File Transfer Protocols
Supports Automating All Major Transfer Protocols
FTP, FTPS, SFTP, HTTP, HTTPS, AS2, Email, SMB, CIFS, NFS
SFTP Server
Host or receive files for secure file exchanges with your clients, customers, suppliers, and other business partners.
External entities connect to your server using any standard SFTP client, using strong authentication and the highest levels of security.
Edge Gateway
No files are ever stored in your DMZ and require no inbound holes in the internal firewall
Securely host an SFTP server AND transfer files between your internal system and external trading partners in a secure, auditable, and compliant manner
Remote Agents
Transfer Files Using Remote Agents
Send files to or from branch locations or partner sites using built-in OpenPGP authentication and encryption, checkpoint restart, and checksum file integrity checking
Secure & Efficient
Secure And Operationally Efficient
Simple interface with options for full alerting, auditing, multi-role administration, file archiving, and extensive logging combine to make operational management pain-free
HIPAA Compliance
The Health Insurance Portability and Accountability Act (HIPAA) established national standards for the security of electronic health care information with both civil and criminal penalties for non-compliance by covered entitles, such as hospitals or physician practices.
PGP Encryption
Best In Class PGP Automation
Encrypt, decrypt, sign or verify encrypted files with a simple checkbox
Cloud Integration
Connect To A Range Of Cloud Storage Providers
Amazon S3, Microsoft Azure, Box, Citrix ShareFile, Dropbox, Google Cloud, Oracle Cloud and more
Enterprise Scheduler
Enterprise Class Scheduling And Folder Monitoring
Schedule jobs down to the minute, including Calendars for exclusions, execution time windows and more, or monitor any accessible shared folder
Workflow Triggers
Comprehensive Source File Selection And Triggers
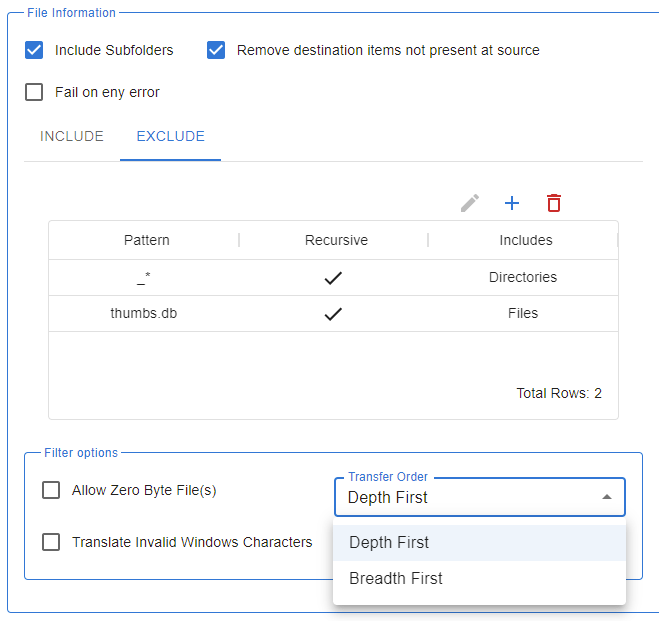
Transfer the right files the first time by selecting by name patterns, dates, sequence numbers, all with support for trigger files for the whole batch or per-file. Specify the order files should be transferred, including time-based or alphabetically.
REST API For DevOps
Control Diplomat MFT Using Its REST API
Initiate, terminate, and monitor file transfer jobs and more from app servers or using your DevOps tools or enterprise job management platforms
Synchronization
Diplomat can synchronize that source directory structure to any number of destinations. Those destinations are often installations of the Diplomat Remote Agent, offering extensive control, very strong security, and a high level of confidence with SHA-256 checksum integrity validation.